- Strategic Thinking (The mental or intellectual process that an individual applies to achieve success in a game)
- Tactical planning (Preparing, coordinating and executing the most accurate and effective plan)
- Industry Knowledge (Expert knowledge of the best threats and tools)
- Social Engineering (Using human vulnerabilities)
- Physical Attacks (Using the best way to penetrate physical systems)
- Virtual Attacks (Developing methods and tools to penetrate virtual systems)
- Malware Development (Malware development and reverse engineering)
- Open Source Intelligence (Intelligence data acquisition through open source intelligence and information available to the public)
- Red Teaming tests focus on using end-to-end attack scenarios. For this reason, scenarios are determined by using weaknesses in more than one area in Red Teaming tests and penetration attempts are made with the determined scenarios.
Unlike a traditional penetration test, Red Teaming does not take a completely technical approach. In addition to the technical approach, it simulates real-life attacks by using all of the components of human relations (social engineering), physical penetration, open source intelligence and target-oriented attack (APT) in harmony. Classic penetration tests are just exercises of red teaming tests. For this reason, the activities, purposes and results of both tests are different from each other. Penetration tests are a technique based test used to reveal security vulnerabilities and compliance issues (mainly configuration). Red teaming tests can also be considered as an integrated structure that aims to progress by including the following test types. This structure is included in the "Graph-1: Red Teaming Natural Dependencies Graph" below.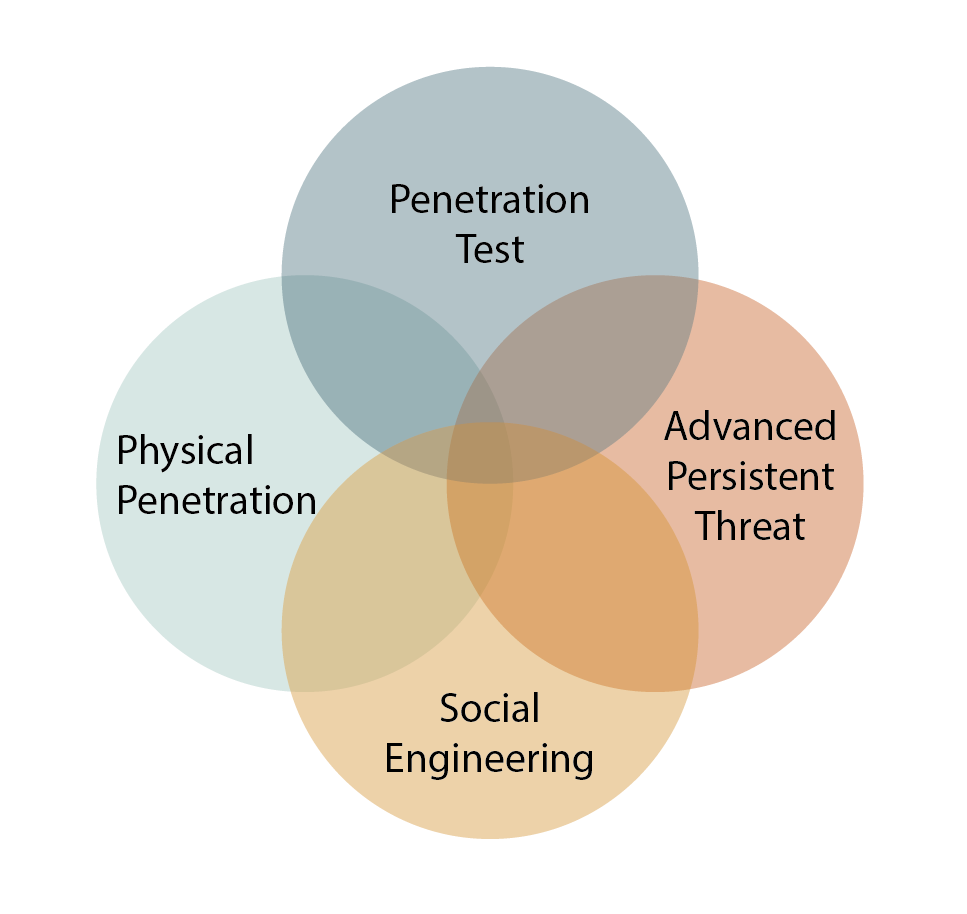
Although there is no internationally appropriate and generally accepted general test methodology for Red Teaming tests, it includes the generally accepted methodological approaches in the graphic above. These methodological approaches are as follows.
- NATO CCDCOE (NATO Cooperative Cyber Defense Center of Excellence)
- US Army Red Teaming Handbook v7
- OWASP
- PTES (The Penetration Testing Execution Standard)
Red teaming tests are expected to be as extended as possible and spread out over time. This approach is critical. It is important that the tests for all known infrastructure systems and personnel using the systems during Red Teaming activities are more effective and realistic. Because the main purpose of the test is to evaluate all the possibilities that may occur in real life and to determine a precaution or strategy against the findings of the test results.
Red Teaming; It is a testing approach that targets vulnerabilities, alternative options, vulnerable areas, systems and users in the organization, and is created to identify limitations and risks as well as evaluate them.
Red Teaming tests are carried out under the following 3 main headings.
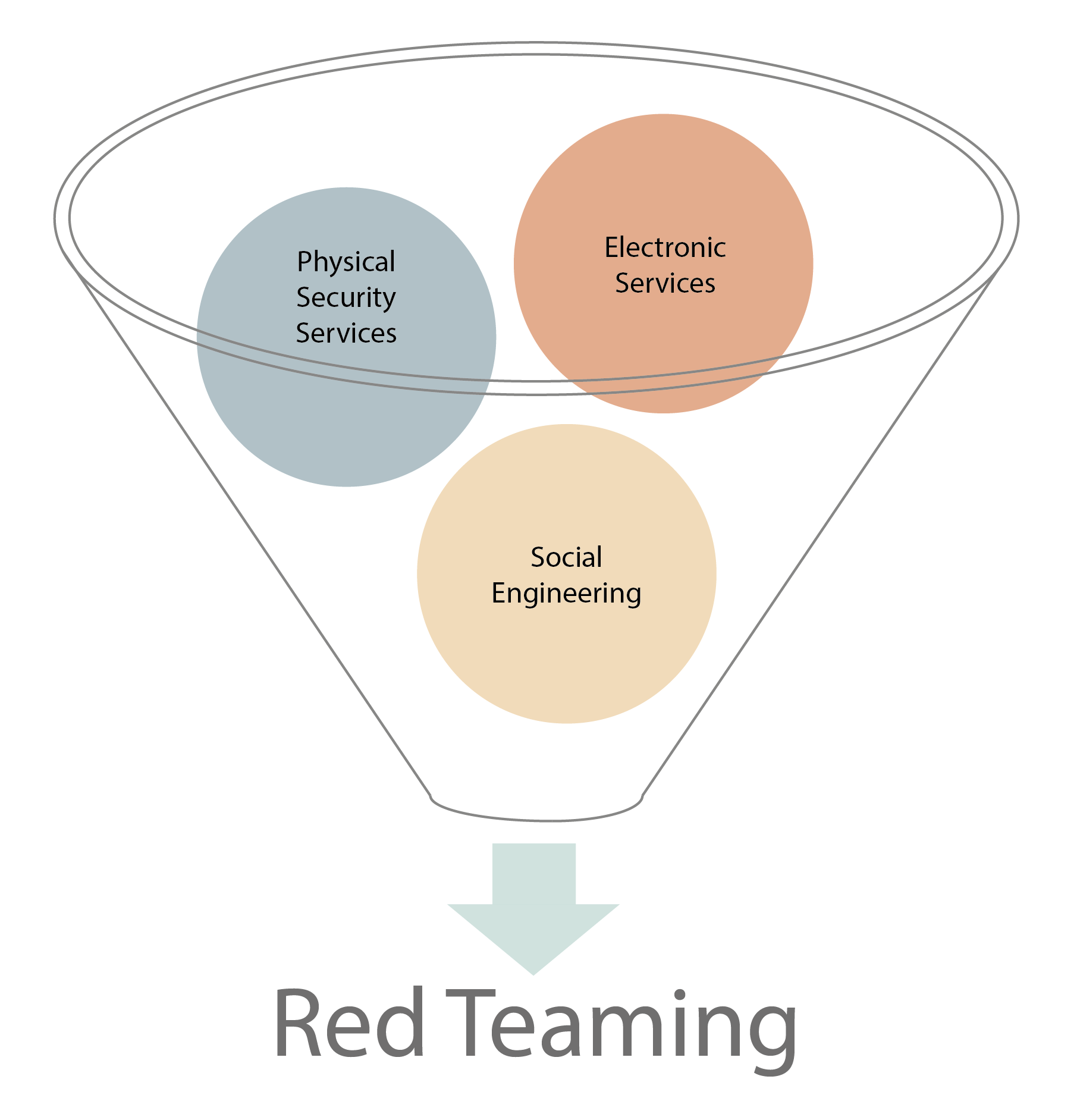
- Electronic Services
- Physical Security Services
- Social Engineering
Red Teaming services and the processes that belongs to these services are given in the graphic named "Graphic-5: Red Teaming Service Subheadings" below.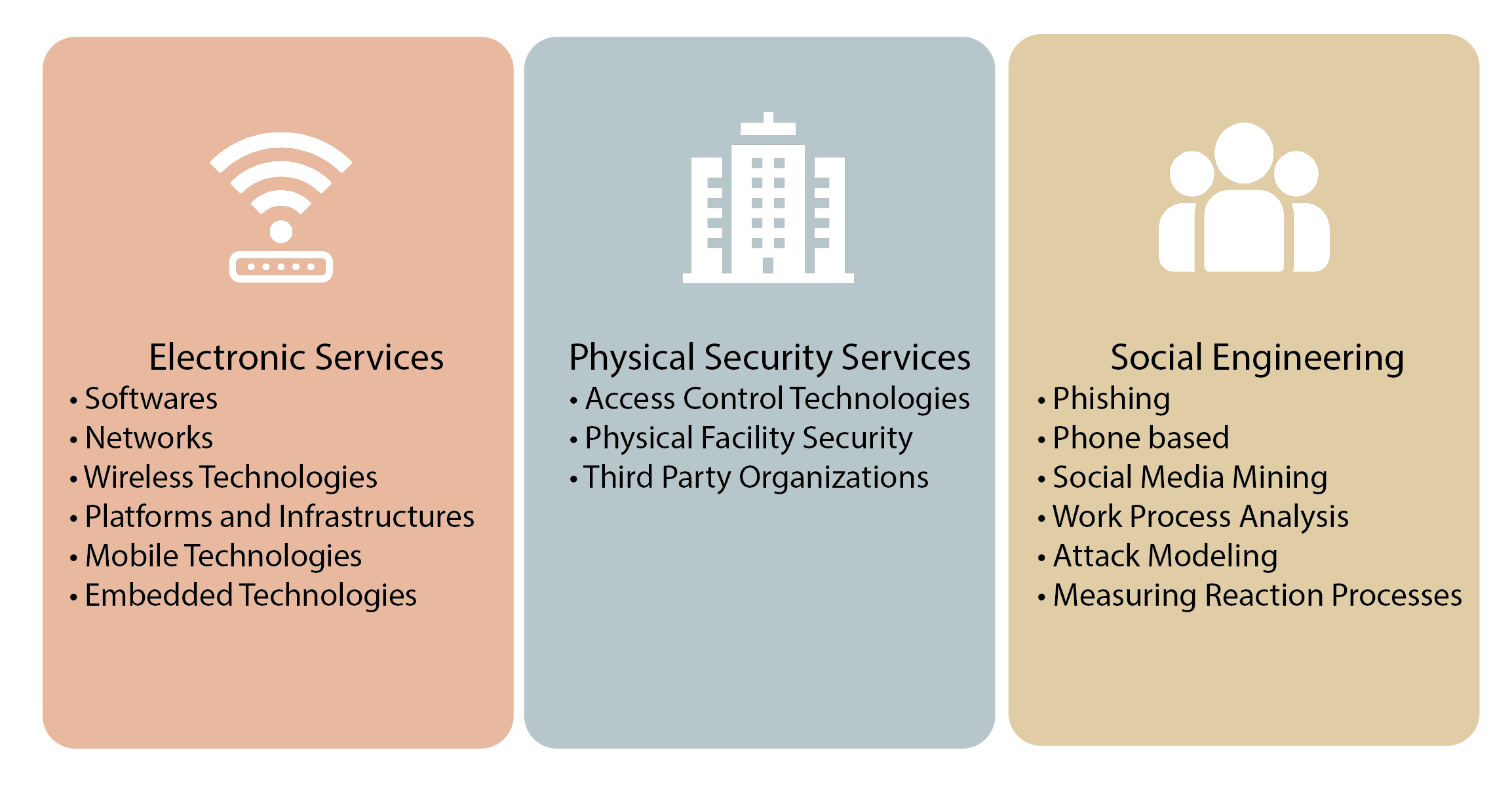
Attack phases of all services and sub-services differ from each other. The attack is carried out by combining the red teaming tests for the platforms detailed under 3 headings with the main scenario.
During the tests, softwares developed specifically for many institutions and publicly open softwares are used, and some hardware tools are also used.
Important Note: Although testing for all assets will make the test more accurate and realistic, it also involves some risks. For example, it may cause unwanted interruptions in production facilities or SCADA networks.
