
Industrial Control Systems (ICSs) are structured as stand-alone as they are not interconnected and do not have security measures priority due to their nature. The Internet and its ubiquitous Internet protocol networks have changed the design of many ICS and made ICS a protected extension of the corporate network. This means that sensitive ICS can be accessed from the internet by malicious people.
A cybersecurity assessment on ICS helps an attacker identify vulnerabilities that could cause the system to malfunction or gain control over the system.
Because of the significant differences between an ICS cybersecurity assessment and testing to be performed in a standard corporate environment, many considerations must be taken into account. For example, various tools used in standard IT systems can cause serious hazards (service crash or unresponsiveness) in ICS. When security tools such as scanners are run on the network, they can cause ICSs to malfunction or stop completely. For these reasons, security audits should be performed on a backup or inactive ICS whenever possible, taking into account the potential implications of testing on a production system. Since the advantages and disadvantages of various alternative vulnerability testing methods for ICSs are also considered, the tests can be tailored according to the ICS features and the needs of the organization.
This document has been prepared to provide information about the tests and process that will take place in the security audits of the Institutions' Industrial Control Systems, Supervisory Control and Data Acquisition (SCADA), Distributed Control (DCS) and/or process control (PCS) systems.
An ICS cybersecurity assessment is significantly different from an IT penetration test, although there are similarities in the tools and methods used. Some of these differences are about the purposes, focus and impact of the tests.
Penetration testing can pose significant risk to ICS systems. At least, it can slow down the response times of networks due to network scanning and vulnerability scanning. Penetration activities can render ICS components inoperable, alter system data, or manipulate the physical system, causing economic or physical damage. Although this risk can be minimized with an experienced penetration tester and an institution-specific methodological approach, it can never be completely eliminated.
Security priorities in IT and OT Systems are as follows:
A standard penetration test; It focuses on the corporate/IT environment and vulnerabilities in open applications that can be accessed by an attacker in an ordinary user profile that is not authorized over the internet. Online penetration testing is rarely a part of ICS penetration testing. ICS/OT systems are located as isolated from the IT and internet environment as possible. The protocols used in ICSs are different from general IT protocols. Firms selling products on ICSs use proprietary protocols for inter-process communication. However, since some protocols used for ICS are built on the TCP protocol, it is known that TCP ports are also open to access in some cases. These protocols have been developed without prioritizing security, assuming that ICSs are isolated from IT systems and the internet environment. Manufacturers think that the protocols used in ICS cannot be used by the attackers. Communication in field devices in Industrial Control Systems mostly uses industry standard protocols such as Distributed Network Protocol 3.0 (dnp3) and Modbus.
These protocols were originally developed to run over serial connections. But it was placed above TCP/IP for the ease and efficiency of LAN/WAN communications. Most of these proprietary and industrial protocols do not have any authentication or integrity checking, and some industry protocols are published with information that is available on the Internet. As ICSs are no longer isolated from the corporate/IT world, these insecure protocols put systems at risk for a cyber attack. Because of this insecurity inherent in ICS environments, security tests performed on ICSs focus on the security of all products and frameworks (all communication paths inside and outside the ICS network) hosted on the ICS. In security auditing, the architecture of the network is evaluated in a broad framework including the use of firewalls and DMZs. The IT and ICS network should not communicate directly, all corporate communications entering and leaving the ICS network should be routed through a functional DMZ or an alternative architecture. ICS LAN has only ICS communication; this network must not have Internet and e-mail access. In penetration tests, vulnerabilities that may cause unauthorized access to the reliable ICS network from the network, servers, applications, IT or DMZ network are detected.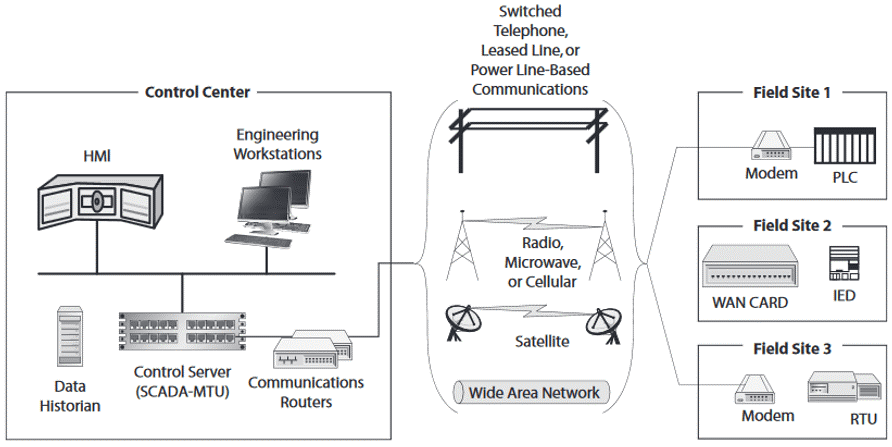
Security Tests to be Performed
In the tests to be carried out, studies are performed on the following subjects;
- Segmentation Analysis
- Visibility Analysis
- Authentication Infrastructure Analysis
- Patch Analysis
- Remote Access Analysis
- Anti-Malware Analysis
- Cyber Incident Monitoring and Response Analysis
